This post provides step-by-step instructions for setting up single sign-on (SSO) from Salesforce to Adobe Sign (formerly EchoSign).
Prerequisites
- Adobe Sign enterprise account with system administrator access. If you do not already have an account, sign up for a free trial here.
- Your Adobe Sign account must have a custom domain in order for single sign-on to function.
- Salesforce org with identify features (developer or enterprise and up) with system administrator access. Sign up for a free developer edition org here.
Step 1: Set up My Domain in Salesforce
The My Domain feature creates a custom subdomain for your org and is required to use Salesforce as an identity provider. Go to Setup -> My Domain, enter a name for your subdomain and click “Check Availability”. Once you get a confirmation that the subdomain is available, click “Register Domain”. Salesforce will send you an email when the custom domain has been registered.
Click the link in the email and log in using your new domain. Navigate back to the My Domain page in setup. Click the “Deploy to Users” button.
Step 2: Enable Salesforce as an Identity Provider
You’ll need a self-signed or commercially signed certificate in order to enable Salesforce as an identity provider. If you don’t already have a certificate in the Salesforce org, you can quickly create one by going to Setup -> Security -> Certificate and Key Management. Click the “Create Self-Signed Certificate. Enter a descriptive name for the label and the unique name will be populated automatically. Click the “Save” button.
Now we can enable the Salesforce org to be an identity provider. Go to Setup -> Identity -> Identity Provider. Click “Enable Identity Provider”. Select the certificate you just created, or an existing one.
Step 3: Get SSO Information from Adobe Sign
Log into your Adobe Sign account and navigate to Account -> SAML Settings.
Under SAML Mode, select the option ” SAML Allowed – users may use SAML but can continue using their Adobe Sign credentials”.
Enter a the value for your custom Adobe Sign domain for Hostname, for example “aaronwinters”.
Scroll to the bottom of the page and note the information in the section called “Adobe Sign SAML Service Provider (SP) Information”. You will need this information in the next step.
Step 4: Create a Connected App in Salesforce
The connected app is going to store information about Adobe Sign and is also going to be used to create the tile in the App Launcher so that users can quickly launch Adobe Sign from Salesforce.
Navigate to App Manager in Setup and click “New Connected App” in the top right of the page. Use the following values
- Connected App Name: Adobe Sign
- API Name: Adobe_Sign
- Contact Email: (any email address)
- Logo Image URL: (click “Upload logo image” and upload an image file that is 125×125 pixels – this will appear in the app launcher tile)
- Enable SAML: true
- Entity Id: http://echosign.com
- ACS URL: https://secure.na2.echosign.com/public/samlConsume (replace “secure” with the value you chose for Hostname in Step 3 above)
- Subject Type: Federation ID
- Name ID Format: urn:oasis:names:tc:SAML:2.0:nameid-format:persistent
- Issuer: this should be your custom Salesforce domain: https://<custom-domain>.my.salesforce.com (may also look like this if you are using a developer edition org: https://<custom-domain>.dev-ed.my.salesforce.com)
- IdP Certificate (Keep default value)
Click the “Save” button.
Next we need to give users access to the connected app. Navigate to Manage Connected Apps. Click the “Adobe Sign” app to open the detail page of the connected app. Click Manage Profiles and add the System Administrator profile.
Finally, we need to set the Start URL for the connected app. Copy the IdP-initiated login URL in the SAML Login Information section of the connected app detail page. Click the “Edit Policies” button. Paste the IdP-initiated URL into the Start URL field and click the “Save” button.
Step 5: Configure SSO Settings in Adobe Sign
Download the Certificate from Salesforce
First, download the certificate you used when enabling Salesforce as an identity provider by navigating to Setup -> Security -> Certificate and Key Management. Click the name of the certificate and then the “Download Certificate” button.
The file downloaded from Salesforce is Base64-encoded with a .crt extension and Adobe Sign accepts the text of the certificate. You can view the text of the public key with the following OpenSSL command in a terminal
openssl x509 -in certificateName.crt -text
From the terminal output, copy the content of your Salesforce certificate between the “—–BEGIN CERTIFICATE—–” and “—–END CERTIFICATE—–” labels.
Update SSO Settings in Adobe Sign
Log into Adobe Sign and navigate to Account Settings -> SAML Settings.
Scroll down to the section called “Identity Provider (IdP) Configuration” and enter the following values:
- Entity ID/Issuer URL: this should be your custom Salesforce domain: https://<custom-domain>.my.salesforce.com (may also look like this if you are using a developer edition org: https://<custom-domain>.dev-ed.my.salesforce.com)
- Login URL/SSO Endpoint : (enter the value of the “SP-Initiated POST Endpoint from the Connected App created in Step 4)
- SSO Certificate: (paste the value of the certificate you copied from your terminal)
Click “Save”.
Create SSO User
In the Account -> Users page in Adobe Sign, create a new user to test the SSO authentication flow. On the “User information” tab enter values for the following fields: Last Name, First Name and Email Address.
Navigate to the user record in the Salesforce org that you are going to use to test single sign-on. This user should be a system administrator, because that is the only profile we granted access to in the connected app. Click the “Edit” button and enter the value of the Email Address you used when creating the new user in Adobe Sign into the “Federation ID” field. Save the user record.
Step 6: Test the Single Sign-on Flow
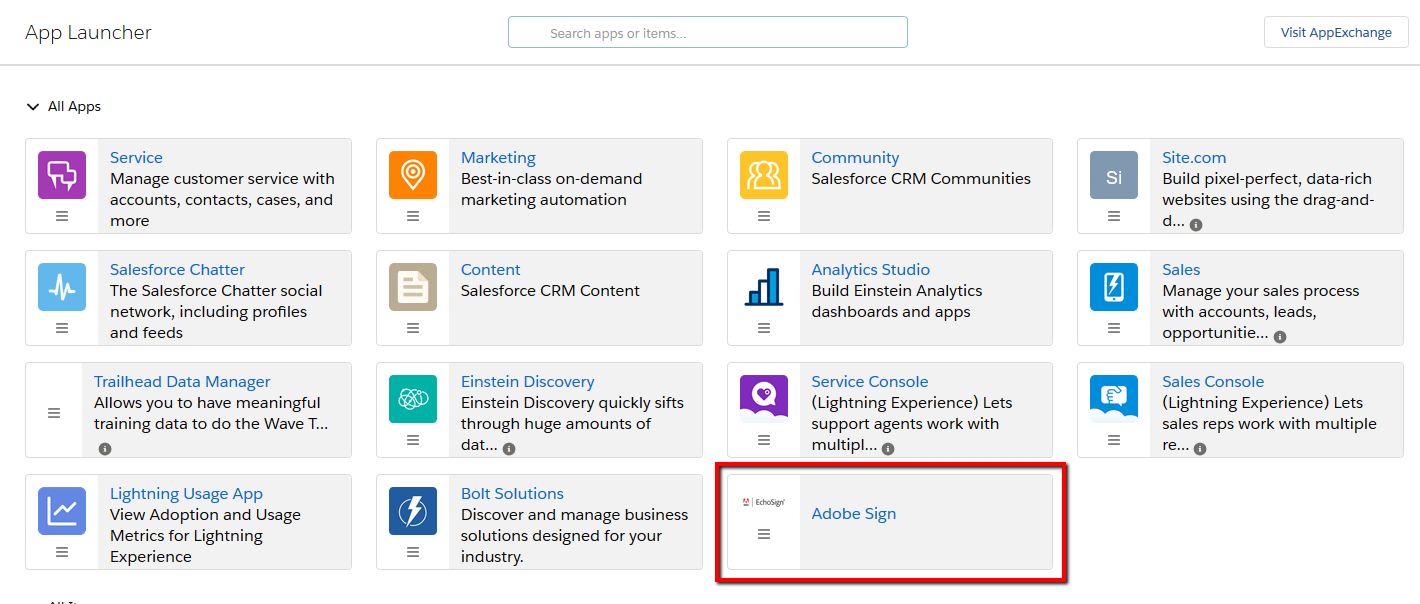
Open the App Launcher. You should see a tile for your Adobe Sign app. Click the tile and Adobe Sign should open and you should be logged in automatically.
Resources
- Salesforce documentation: App Launcher
- Adobe documentation: Enable Single Sign-on with SAML
- Adobe documentation: Adobe Sign Domain Claiming



What a great article, easy steps. I followed and now able to set up SFDC-Adobe Sign
Would you mind adding the below?
1) Make sure domain is whitelisted in Adobe Sign side, if not Adobe Sign will throw a message Corporate Sign on Failed
2) It seems, Adobe Sign does not expect any SAML attributes. It just expects SAML NameID which is actually an Email that acts as a unique Identifier. So, select Federated ID in Subject type and SAML:2.0:nameid-format:persistent.
3) Go to User detail page and under Federated ID, I paste the email of user. Without doing this it will fail to log in for me with the above error message.
Thank you
Mr Anonymous